Let say you are thinking of purchasing something online or you are not sure in general about the safety of a certain website. How can you tell? I just came across this little page that Google has for their Safe Browsing…
http://google.com/safebrowsing/diagnostic?site=weebly.com/
In this case I have weebly.com in the query because it is good to know if your “free” website host also allows malware or has a history of it. If you put wordpress.com in there you will see similar results. Although not as drastic.
http://google.com/safebrowsing/diagnostic?site=cswtech.wordpress.com/ looks clean as a whistle 🙂
Have a great day.
- Category Archives Security
-
-
 Using OSSEC to Detect MacDefender in Squid Logs
Using OSSEC to Detect MacDefender in Squid Logs
While doing forensics this week to determine where the MacDefender malware was coming from I noticed one thing that was distinct to all the requests for this malicious package. When it was downloaded the mime type for the file request was “application/download” when searching through the logs I noticed that this was a mime type that I would want to know about anyways and that generally there are not a lot of requests associated with this mime type. So I would not be overwhelmed with notifications.
So how do I monitor this? I’ve been using the OSSEC IDS system (https://www.ossec.net/) for a few years now. It is an excellent tool and completely customizable. To get OSSEC to monitor my squid log first I added the /var/log/squid/access.log to the list of monitored files in the /var/ossec/etc/ossec.conf file and restarted the service.
<localfile> <log_format>squid</log_format> <location>/var/log/squid/access.log</location> </localfile>Now, the problem I found with adding this is if you have a pretty busy network with a lot of different clients (Macs, Linux, PCs) then you are going to get some odd traffic that will trigger alerts based on multiple errors found in the squid access log. To monitor this it would be a good idea to shut off active response for a while and then gather some exceptions that you can put into the local_rules.xml file on the OSSEC server. Below is the rule I used to detect application/download.
<group name="squid-custom,"> <rule id="100400" level="6"> <if_sid>35000</if_sid> <match>application/download</match> <description>Application downloaded via squid proxy. Check URL to determine malware.</description> </rule> </group>
I have I have email notifications set for level 6 and up and active response to 7 or greater. This way internal hosts will not lose there internet connection abilities when downloading a legitimate program. Below are some of the exceptions that I had to add to the local_rules.xml to make sure that certain requests did not add internal hosts to the hosts.deny file.
<rule id="35057" level="0"> <if_sid>35057</if_sid> <match>secars.dll</match> <description>False Positive. Symantec Endpoint client going through proxy.</description> </rule> <rule id="35009" level="0"> <if_sid>35009</if_sid> <match>secars.dll</match> <description>False Positive. Symantec Endpoint client going through proxy.</description> </rule> <rule id="35008" level="0"> <if_sid>35008</if_sid> <match>secars.dll</match> <description>False Positive. Symantec Endpoint client going through proxy.</description> </rule>
There will probably be a few more things to add. Just monitor your alerts carefully and you will have it smoothed out in short order.
As I was about to leave work today I received an alert from OSSEC that looked like what you see below. I’ve edited out the internal information and the bad URL’s host.
OSSEC HIDS Notification. 2011 May 27 14:49:17 Received From: (MyProxy) IPaddress ->/var/log/squid/access.log Rule: 100400 fired (level 8 ) -> "Application downloaded via squid proxy. Check URL to determine malware." Portion of the log(s): 1306522093.290 620 <InternalHost> TCP_MISS/200 47939 GET http://VeryBadHost.com/files/a6930dd67bda35bd60e694db3a40ec58d3875a870e2210c7.zip DIRECT/<BadIPAddress> application/download --END OF NOTIFICATION
I blocked the IP on my network, checked the host that downloaded the package and then submitted the bad ip address to the Google Safe Browsing Report here:
-
 Macintosh Fake Anti-Malware: How to Protect Yourself and Your Network
Macintosh Fake Anti-Malware: How to Protect Yourself and Your Network
Protection at Home: (For the regular home folks)
There is a new Malware scam going around for Mac computers that exploits Safiari’s “Open safe files automatically” feature. If you are just a home user and use Safari then please disable this risky feature . In Safari() just go to the Menu: Safari->Preferences and under the General tab un-check the option near the bottom.Protection at Work: (For Network Administrators and other Geeks)
So what if you are like me and you are in charge of a whole network full of Macintosh machines? Well hopefully your settings are managed with Open Directory and you use Workgroup Manager to enforce certain settings. I have a variety of User and Computer groups that are managed in this manner. In order to manage Safari settings in Open Directory you need to add the Safari.app to the preferences under this screen which you see when you click on a group, then preferences(Note: Click on the details tab).Choose Safari in the /Applications folder. (Note that I have also previously chosen /System/Library/CoreServices/Managed Client.app which is why there are a lot more options on this screen.) Once Safari is added, highlight com.apple.Safari and click the Pencil
In the next dialog highlight the “Often” and then “New Key”. Choose the “Open Safe Downloads Automatically” and change the value to false. Apply it and click Done. This preference will now be set each time a managed client opens Safari. End-users can still un-check it if they like, but it should be reset after a quit and reopen.

I’m not sure why this option is not available under the “Always” section, which would lock the option. Feel free to explore the other options available under the “Always” key.Filed under: Computer Security, For-Facebook, For-My-Facebook, Macintosh
Category: Computer Security, For-Facebook, For-My-Facebook, Macintosh, MacDefender, malware
-
 Online Accounts: Just a Bit of Common Sense
Online Accounts: Just a Bit of Common Sense
Millions, possibly billions, of people are conducting transactions online. Whether this is online banking, shopping, social networking or group discussions there are a few important guidelines to follow in order to make sure that your information and accounts are only going to affect the scope of the site you use them on. In other words do NOT use the same username/password at multiple sites. In the last week alone there have been three larga data breaches that involved either employee or customer information. For an example just Google: texas OR barracuda OR epsilon data breach.
Account Choices:
For my very important accounts I never use anything remotely close to a real name when choosing my username. The same applies when I am choosing a password. I never will use the same password that I used on another site. Why? Because when something happens at the site with whom I am engaging services with is hacked or left wide-open I do not want my username password to be valid elsewhere. For instance, say I have an account with Citibank or some other online banking firm and somehow that site’s information is extracted by a group of online criminals. I want this breach to stop within the scope of that institution and not have those credentials move onto another popular website.
Choosing an account name and password. Your usernames and passwords need to contain alpha, numeric, upper case, lowercase and special characters(These things:!@#$%^&*). When I am making a password I have a couple approaches. One approach is to choose a fairly long phrase or lyric that I like and use the first initial of each word to create my password. I’ll alternate upper and lower case and put in a few 1′s for I’s or zeros for O’s. Sometimes I’ll phonetically alter the spelling and combine acronyms. For example: RUr34llyPhour2dazeOld? (English Translation: Are you really four days old?) Another approach that I use I like to call is a Brain-Fart-on-my-Keyboard. Just start pressing random keys on the keyboard while thinking random things. I usually end up with something like this…
User: Lhjglkj(*&y43tiy678e
Pass: z7834hKJGjkG78efuhff%YThese are things I will never remember and if possible they will never be lifted from my mind. I save these passwords in an encrypted file that I do know the password to (that is another story) and then simply copy/paste them into the sites that I am logging into. An easy way to do this would be by using the highly rated free program LastPass: https://lastpass.com/
The point to all this: Do not use a real word or name!
Those Stupid Questions they ask:
One thing that is really annoying are those security questions that they ask you to fill out. Such as what is your Mother’s maiden name, etc… If they ask you to create your own question I use the “Brain Fart” method above for the question and the answer. If it is one of those choose a drop-down question and then they make you type your answer it’s another brain fart for me…
Filed under:
-
 Specialized Email Phishing Attacks Highly Likely
Specialized Email Phishing Attacks Highly Likely
This week many of you have received emails from companies (Best Buy, Chase, Citi, Disney, Walgreens, TiVo, etc, etc..), whose website’s you’ve registered with with that mentions a data or security breach in which your Name and Email address was stolen from a company called Epsilon. Epsilon is a company that send out gazillions of emails for a lot of companies(About 2,500). Simply they are a very busy email marketing delivery service with a lot of personal information.
The Problem: Since these criminals now have your name, email address and the actual company associated with that information, you can expect that they will be sending you email communications posing as a legitimate company. I’m not going to get in to the technical aspects of how they will do this, just know that they can and will.
The Solution: In a previous blog post I mentioned phishing attacks that appear to come from a legitimate source yet do not. In that post I summarized at the end a few things that you should do to be cautious and protect your information/identity from being stolen. What I really should have said is simply: Do not click on links in an email*.
If you get an email from your bank, read it, maybe it is real (Do you always believe everything you read?) and something you need to take care of. Instead of clicking on that convenient link in the message, manually open your web browser(hopefully you use Firefox or Chrome), go to the companies site that you should have bookmarked and take care of business.
For a fairly complete list of companies that were exposed check this website: http://www.databreaches.net/?p=17374
For more on Phishing attacks the FBI.gov site has a good example: http://www.fbi.gov/news/stories/2009/april/spearphishing_040109
If you want learn more about computer security I recommend this weekly podcast: http://twit.tv/sn . They have hundreds of shows online with notes: http://wiki.twit.tv/wiki/Category:Security_Now_Show_Notes
——————————————————-
* Unless of course you know what message headers or HTML source code are and how to decipher what they actually mean. I only look at them since it is part of my job and I am curious. In reality, it is easier and safer to just go to the companies website manually.
Filed under:
Category: Computer Security, For-Facebook, For-My-Facebook, Phishing, Email, Epsilon, phishing
-
 Security Note: Fake SSL Certificates Issued for 9 Popular Websites
Security Note: Fake SSL Certificates Issued for 9 Popular Websites
Apparently Comodo issued security certificates for these popular websites…
login.live.com,, mail.google.com, http://www.google.com, login.yahoo.com (3 certificates), login.skype.com, addons.mozilla.org. This would allow attackers to create fake websites using these certificates and pose as authentic site and at least steal your logon information.So when your Microsoft Update asks you to install an update out of make sure you do(That little yellow shield near the clock). If you do not want to wait for the update to come to you then go get it here…
http://support.microsoft.com/kb/2524375
In addition, make sure you update your Firefox Browser as well. Mozilla Firefox released 3.6.16 today also to include a fix that “blacklists a few invalid HTTPS certificates”. The Firefox 3.6 update is available here: http://www.mozilla.com/en-US/firefox/all-older.html
Or just simply update to the latest version: http://www.mozilla.com/en-US/firefox/new/References:
http://www.wired.com/threatlevel/2011/03/comodo-compromise/
http://support.microsoft.com/kb/2524375
-
 Avoiding Phishing Scams That Look Like Facebook Notifications
Avoiding Phishing Scams That Look Like Facebook Notifications

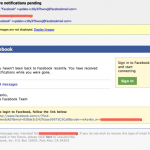
Social network users need to pay close attention to links that come to you via a social network website. There are several Phishing scams circulating that will trick you into clicking on a misleading link in a message. Sometimes the link is just to show you something that they are trying to sell, or infect your machine with a malicious program such as a virus or trojan. By default facebook notifications come to the email account that you signed up with. For me this is not a big deal. I just used an inbox that I use for nothing but junk and rarely do I visit it, but there are several that will check an email account daily if not more and have “notifications” in the inbox that will be clicked on regularly. Below is an example email fake facebook notice. It looks genuine. I should know. My wife clicked on it before I could tell her that it wasn’t real 🙂
This email looks like it is from facebook. The return address has facebookmail.com in it just like all the other messages you receive from this website. So what do you do? The first thing you need to do is just hover your mouse over a few of the links (do NOT click on them) and see if they actually read the same in the hover as they read…


You can see from these examples that if you click on these links it will send you to a site that is anything but facebook. The domain: campus.2kool4u.net is where this goes. If you click on it the site will redirect to a site selling viagra. If you look at https://whois.domaintools.com/2kool4u.net you see that the 2kool4u.net domain hosts quite a few different sites. This looks a tad “phishy”. Try googling these keywords: 2kool4u.net scam and all you seem to find is junk and more junk.
Summary/Options:
- Do not click on links in an email
unless you are sure that it is a good link. - Turn off your notifications or just trash them and manually go to the social networking site and look at your updates.
- Turn off HTML email in your mail program if you can. There should be an option to view mail as “plain text”. This is inconvenient, but it removes the fake links from the message.
Note: Edited on 4/9/11 to change #1 and #2 in the summary. Simply do not click on links in an email. Explanation on this newer blog post.
Filed under: Computer Security, For-Facebook, Internet, Phishing, Social Networking
- Do not click on links in an email
-
Can the Conflicker Worm be removed?
By crmanski
Over the last few months I have seen and heard or quite a few computers infected with the “Conficker” worm ( also know as Downup, Downadup and Kido). It is truly a nasty piece of software that ingrains itself so far into the system that it has been impossible to remove from any of the systems that I had not personally secured myself with the steps I outline here. That one machine the person had actually clicked on the “yes” button to install the worm. Luckily it was with the non-administrative account and I was able isolate the files and remove them.
I did some research around the web on so called removal instructions and came across Microsofts…
microsoft.com – “How do I remove the Conficker worm? If your computer is infected with the Conficker worm, you may be unable to download certain security products, such as the Microsoft Malicious Software Removal Tool or accessing certain Web sites, such as Microsoft Update. If you can’t access those tools, try using the Windows Live OneCare Safety Scanner.”
This is totally useless. I’ve spent hours using a manually downloaded MSRT and the Live OneCare Scanner. It might tell you that it cleaned the machine and the everything will look good, but after a couple reboots and even opening Internet Explorer once will bring it right back. You might be able to “remove” it, but the problem of Windows XP or Vista setting up all home user account as administrators of the local machine still exists. The point of infection is still available and any account that uses the computer can infect the system. Try to remove this infection is an exercise in futility.
If you have been infected I think it is best if you backup your documents and re-install the Operating system from scratch (Don’t forget to scan them with an updated Antivirus before putting them back on your computer). This way you can be truly sure that there is no infection. It is not wise to trust a machine that has had such a bad infection. This is especially true for someone who does online banking or conducts other business transactions on the Internet. It is better to start fresh and make sure that the system is secure. Follow the steps on the checklist. If you cannot, then find someone that can.




